Applied Explanation of the “Cyber Kill Chain” Model as a Cyber Attack Methodology
The rapidly changing threat environment, complexity and increasing frequency of cyber attacks in cyberspace have caused cyber security applications to be integrated into a comprehensive system that includes detection, prevention and response processes.
Most organizations have tools to detect known attacks, but again, a few of them can happen. However, detecting and stopping cyber attacks whose attack signatures are not defined to security systems or whose behavior patterns are changed to make it difficult to detect attacks with defined attack signatures is a challenging area of cyber security. For this reason, institutions and organizations are looking for better tools and ways to create their own threat hunting teams, constantly improve their defense techniques, and keep their digital assets safe.
Understanding how cyber attackers work provides a good input for organizations to determine their cyber defense models. This model shows how organizations can detect, stop, disrupt, and recover from an attack, and where security operations need to be strengthened. All these needs led to the development of the Cyber Kill Chain model.
Cyber Kill Chain is a term originally of military origin and was used in military terminology to indicate the stages that the attacking party went through during the attack. In 2011, Locked Martin company published an article explaining the attack methodologies of cyber attackers by applying these stages to the cyber space. The idea behind the Cyber Kill Chain theory is that by understanding each of these stages, cyber defense units can better identify and stop attackers at each of the relevant stages.

Applying the Cyber Kill Chain model to the organization’s cybersecurity ecosystem enables organizations to understand how they can increase their security by capturing and stopping threats at every stage of the attack lifecycle. This model guides security teams to establish the chain of attacks at any step of the process to break the attack.
Reconnaissance Phase
This stage can be defined as the target selection stage, defining the target organization details, industry-vertical-legislative requirements, information about technology choices, social networking events or mailing lists are the areas researched.
The attackers are basically looking for answers to the following questions;
“Which attack methods will work with the highest degree of success?”
and “Which is easiest to execute in terms of our resource investment?”
Application-1 Recon
Note: This phase can be repeated and expanded as the attack evolves. You will see examples of this during the application.
Suppose a company is specified as the target. Attackers will try to collect the necessary technical information for active reconnaissance activities by doing passive discovery about the website of the relevant company.
Passive Reconnaissance: It is the collection of information on the internet with open source information collection methods “OSINT” and collecting information without interacting with the target system.
Active Reconnaissance: As a result of the information obtained as a result of the passive, service, weakness, etc. in the target. scans are performed by scanning tools (nmap, nikto, etc.).
In our example, by searching the information of the target website at “whois.domaintools.com” IP information, who it is registered to, etc. information has been accessed.
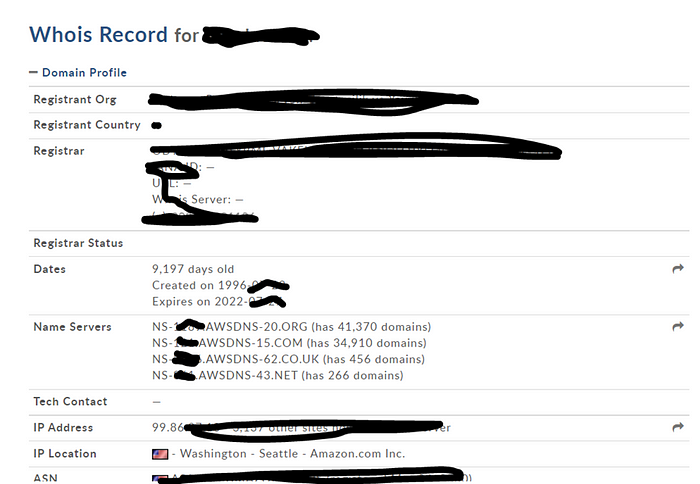
The company’s website registration date is prety old, giving attackers clues that there may still be older generation operating systems in the company. It is planned to send malicious software to the company e-mails of the company employees, which allows the hijacking of “windows 7” systems. Before the second stage, the “weaponization” stage, the discovery will continue and the e-mail addresses of the company employees will be scanned by passive methods.
The fact that the company’s website was in the amazon cloud was the second piece of information to direct attackers to user computers that were likely to be more insecure.
With the OSINT tools on the Kali Linux operating system, a lot of research can be done about the target system, including e-mail addresses.
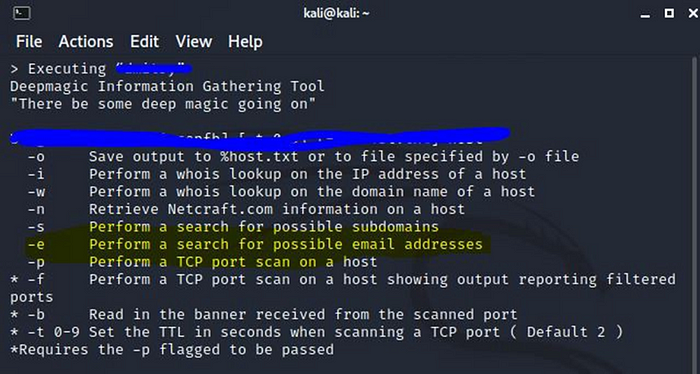
Weaponazition Phase
This step can be accomplished in many ways. Web application exploit, off-the-shelf or custom malware (downloaded or purchased for reuse), or malicious files created by exploiting document vulnerabilities (offered in PDF, Office, or other document formats) are obtained during the discovery phase for use in the next phase, Transmission phase. prepared according to the information.

In the example above, the attackers create the malware with the relevant tool. In the LHOST part, there is the IP address of the attackers’ command and control computer. When the malware runs successfully on the target computer, a session will be opened to the corresponding IP address from the victim computer to the command and control server.
At this point, attackers often use 443 port as a listening port. In this case, Firewalls that do not perform “SSL Inspection” can be bypassed. The signature of the attack is complicated by encoding (shikata_na_nai in the example) to deceive the victim computer’s antivirus system. Therefore, the use of behavioral/heuristic endpoint security products is important.
Delivery Phase
Two basic scenarios are on the agenda during the delivery phase. In the first scenario, malicious files are sent to users by attackers, such as e-mail, etc. and victims are expected to open/run the relevant files. In this scenario, another important delivery method is to allow victims to visit malicious web applications/pages created by attackers. (Watering Hole etc. attacks)
In the second scenario, SQL injection, PHP backdoor upload, etc. They actively send code and files to the target with these methods. At this point, the reaction of the target system users is not expected, the target server / application vulnerabilities are directly exploited by the attackers.
According to the attacker application scenario, at this stage, they send the files they created during the preparation of the attack tools to the e-mail addresses they obtained during the discovery phase.
Exploitation Phase
After the malicious code or file is delivered to the target, it will have to find a place for itself in the target system environment. An unpatched operating system, a web application that is not protected with necessary security measures, and a security-problematic source code will allow malicious file/code to become operational by exploiting security vulnerabilities. Although zero-day attacks are used in some rare cases, security vulnerabilities in the environment are often the path to success for attackers.
In our example scenario, there are three interconnected situations that lead attackers to success. The first reason for the exploit to be successful is the use of the windows7 operating system without the necessary updates. However, this situation alone is not enough. The second situation is that the antivirus system used as endpoint security cannot perform behavioral analysis. The malware, whose signature was complicated by encoding, was able to exploit the vulnerability in the operating system without being blocked. When we look at the network topology, it should be expected that the firewall in the environment will prevent the session opening out of the network, but in this scenario, the FW administrators do not take the necessary measures to analyze the traffic passing through the 443 Port, creating the third situation and the attackers can successfully log on to the target system remotely.
Instalation Phase
The installation phase usually starts with the installation of malware on the target computer operating system. If the malware is an executable or based on malicious code injection or an insider threat, the installation phase is not necessary.
However, if the malware needs to be installed on the target computer, the payload that enables the malware to be downloaded must have already been sent during the delivery phase, and the exploit bypass security systems must be disabled and a bridgehead in the operating system must be found, providing the environment that allows the installation of the malware.
At this stage, the malware installs and the downloaded files either use the operating system’s libraries and support files. In addition, the malware installation updates the operating system’s file access mechanism using privileged access rights. Also, the malware alters the appearance of its files by changing the file’s format or hiding these files from user access.
In addition, advanced malware can alter its trace in memory to avoid detection by sandbox or behavior-based anti-malware systems. These malware are also called polymorphic malware or metamorphic malware respectively.
Polymorphic malware does not change the payload of the malware, but changes the header so that it looks like a regular file in memory. Metamorphic malware also changes the model of the load in memory.
Malware self-protection:
Despite the convenience provided by virtual environments, more recent malware tries to detect if it is
being analysed in a virtual environment and hides its behaviour. The most common parameters checked by
malware are registry keys, memory structures, communication channels, specific files and services, MAC
addresses and some hardware features.
Some examples of these parameters for VirtualBox are:
• Registry keys:
• Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Oracle\VirtualBox Guest Additions
• Computer\HKEY_LOCAL_MACHINE\HARDWARE\ACPI\DSDT\VBOX__
• Processes:
• VboxService.exe
• VboxTray.exe
• Files:
• C:\Windows\System32\drivers\VBoxMouse.sys
Referance:
The installation phase not only installs the backdoor into the target victim, but also ensures that the threat actors are in constant communication with the victim computer.
Also, this phase is different from the exploit phase due to the locality of the activity, i.e., during the installation phase, the payload starts to take hold inside while the exploit phase detects that the malicious package is ready for installation and all the requirements of the exploit phase are met. Also, a permanent connection is established with the server to initiate command and control communication.
Command and Control Phase (C&C)
Command and control networks can be servers, peer-to-peer networks, or social media servers. Also, there can be multiple command and control networks (eg bot networks) to avoid detection. There are malicious attacks that aim at the command and control stage as follows:
a. Information (passwords, financial data, intellectual property, etc.) on the target computer is seized. , eg. keyloggers, Zeus, and Trojan.
b. Sending commands to the malware on the target computer to spread the malware to other parts of the network connected to the target computer, execute the malware, or enable encryption for ransomware activities.
Cybersecurity personnel should consider that the C&C phase is the final phase of blocking malicious activity. The C&C phase takes place similarly to normal internet communication.
Command and control networks can be servers, peer-to-peer networks, or social media servers. Also, there can be multiple command and control networks (eg bot networks) to avoid detection. There are malicious attacks that aim at the command and control stage as follows:
a. Information (passwords, financial data, intellectual property, etc.) on the target computer is seized. , eg. keyloggers, Zeus, and Trojan.
b. Sending commands to the malware on the target computer to spread the malware to other parts of the network connected to the target computer, execute the malware, or enable encryption for ransomware activities.
Cybersecurity personnel should consider that the C&C phase is the final phase of blocking malicious activity. The C&C phase takes place similarly to normal internet communication.
Attackers can vary their tactics and techniques to evade detection. They can use compression mechanisms to hide data. However, the common denominator in the attack is network traffic, and although an endpoint security mechanism cannot detect the presence of a communicating malware, network security systems can do the detecting work.
Actions on Target
This is the final stage of the chain and is responsible for carrying out the objectives of the attack. At this stage, if the malware is deployed on the target computer, it begins to perform the programmed function either through instructions from the command and control server or independently.
The main categories of actions that fall into this phase are:
a. Data theft: stealing private and intellectual data from the network.
b. Ransomware: Threat actors hold victim data hostage and demand ransom payment by encrypting the victim’s data, changing their credentials, or blocking network resources using various encryption methods.
c. Cyber terrorism: threat actors do harm by deleting data or completely corrupting files.
Final Notes:
It is very important not to focus on the traditional single cyber kill chain model in security analysis; A holistic approach should be taken about multiple cyber kill chains (persistence) while taking precautions against threats.
Also, it should be important to understand the attacker’s intentions rather than looking at what the attack is doing. For example, if the attack motivation is to steal financial information from servers, there will be command and control communication going outside of the network, leaving traces for detection in a well-controlled network security system.
LEARN CYBERSECURITY IN 2024
Check out our comprehensive cybersecurity course and enhance your knowledge in the field! Join now to learn the essential skills and techniques to protect yourself and others in the digital world. Don’t miss this opportunity to become a cybersecurity expert!